How to Clone an Android Phone: Proven Ways Without Physical Access

Whether you’re looking to transfer data to a new device, back up your phone’s content, or monitor your children’s online activity, knowing how to clone an Android phone is a useful skill.
Our smartphones are an extension of ourselves. Containing a wealth of personal information and memories, they know almost everything there is to know about us. It’s no wonder that many people want to duplicate that data, whether for legitimate reasons or otherwise.
This article aims to provide you with that know-how. We explain what phone cloning is and different ways to clone a phone, as well as the legal and ethical issues of this controversial practice.
And, as the idea of someone illegally cloning your phone without you knowing is rather alarming, we also discuss how to prevent your phone from being cloned.
So, let’s get started!
-
-
What is Android Phone Cloning?
The Cambridge Dictionary defines cloning as ‘the process of creating an exact copy.’ And that’s what phone cloning is: it’s replicating everything on one phone and transferring it to another.
Imagine taking your whole online life – data, apps, messages, contacts, location, everything – and copying it onto another phone. That’s the crux of phone cloning.
If that sounds scary, it should. There are several legitimate reasons why someone might want to clone a phone, but there are many gray areas and some unquestionably illegal ones.
Why Would You Want to Clone a Phone?
Even though there are legal, ethical, and technical issues associated with copying a phone’s data (which we cover later), many people still do it, and generally, for legitimate reasons.
1. Data Migration
Let’s be honest. Who wants to go through the hassle of manually transferring all the data on your old phone to your new one? With cloning, you can easily transfer all your settings, apps, and data from your old phone.
2. Protecting Confidential Information
You may also need to back up your phone if it contains confidential data, such as sensitive work documents or financial information. In fact, some companies may insist on it if you have a work phone.
Cloning your phone can be a lifesaver if it’s lost, stolen, or damaged, as you can simply restore the cloned data onto a new device.
3. Protecting Children Online
Unfortunately, cyberbullying, especially among young people, is on the rise. And shockingly, only 40% who experience it report it to their parents.
It’s no wonder parents are increasingly concerned about their children’s safety. Phone cloning helps parents monitor their children’s online activity and ensure they’re not exposed to anything inappropriate or dangerous.
4. Tracking Family Members’ Location
Many families use cloning technology so they can track each other’s location. It provides peace of mind. For example, if your partner’s job involves driving long distances, your children are driving to concerts, off on a road trip, or going on dates.
5. Detecting Vulnerabilities
Technical experts and white-hat and grey-hat hackers clone phones to detect any vulnerabilities criminals could exploit. Once found, they can develop and test solutions to fix these bugs and roll out software updates with improved security.
6. Illegal and Unethical Reasons
Unfortunately, some people have far less honorable reasons to clone Android phones:
- Identity theft: Information such as financial details, passwords, and social media accounts can be used to commit fraud, causing you reputational and financial damage.
- Intercepting confidential communication: Private conversations, classified information, and commercial data can be misused for purposes such as espionage, insider trading, or blackmail.
- Intellectual property theft: Trade secrets, design plans, and proprietary information can be sold to the competition.
- Stalking: Complete control over a person’s mobile activity can be used to invade their privacy and harass them.
If you believe Hollywood, people clone phones all the time. It seems nifty, but it’s not always done for the right reasons, raising ethical and privacy concerns.
Ethical Considerations and Legal Implications of Android Phone Cloning
Phone cloning is a serious issue that violates privacy, damages trust, and can be misused by criminals.Ethically, cloning another person’s phone without their knowledge or permission violates their right to keep their personal information private.
Legally, by cloning someone’s phone, you’re committing identity theft and fraud, serious crimes with serious penalties. You may also open yourself up to civil lawsuits for invasion of privacy, financial loss, or emotional distress.
Also important is that criminals can use cloning technology to steal personal information and for more serious activities such as drug trafficking, money laundering, or terrorism. The consequences of these actions can be devastating to society as they undermine public safety and security.
These ethical and legal concerns have prompted governments and law enforcement agencies around the world to implement measures to combat phone cloning. They include:
- stricter regulations on the sale and use of cloning devices
- increased penalties for those caught using cloned phones
- improved cybersecurity protocols to prevent unauthorized access to personal data.
The Difference Between Cloning and Hacking
While terms like ‘cloning’ and ‘hacking’ are sometimes used interchangeably, in the cybersecurity world, they’re very different things.Phone cloning is a legitimate process if you’re cloning your own phone or have the owner’s permission to clone their phone. You might do this to transfer data between an old and a new phone.
Hacking is a completely different story. It’s gaining access to a person’s phone, system, or network with or without their consent by exploiting vulnerabilities or weaknesses in security. When consent is not sufficiently given, hacking is illegal.
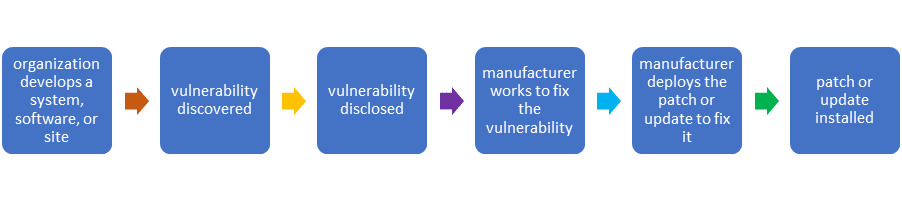
How to Clone an Android Phone Step by Step
So, how do you clone an Android phone? Well, there are a few phone cloning methods (some of which are legal and some not). Here’s a quick overview of some of the approaches:
- Cloud services: Android services like Google Drive and Samsung Cloud can back up your phone’s data so you can restore it to another device. It’s a great method for transferring important data like files, photos, and contacts from your old phone to a new one.
- Remote cloning apps: You install these third-party apps on the phone you want to clone and the destination phone. The data is usually transferred through a Wi-Fi or Bluetooth connection.
- Network-based cloning: Usually used by hackers to exploit network vulnerabilities and bypass digital security systems. Often illegally, but sometimes as part of legitimate pen-testing efforts.
- IMEI cloning: It isn’t possible to clone this identification number. However, you can clone other ID numbers on a phone’s SIM card. Using the cloned SIM card in your phone gives you control over the original phone.
Cloud Services
Cloud services, such as Google’s, store most of your data in the cloud, and phones generally now have a built-in backup and restore feature, making it easy to back up everything on the phone you want to clone and restore it to another one.
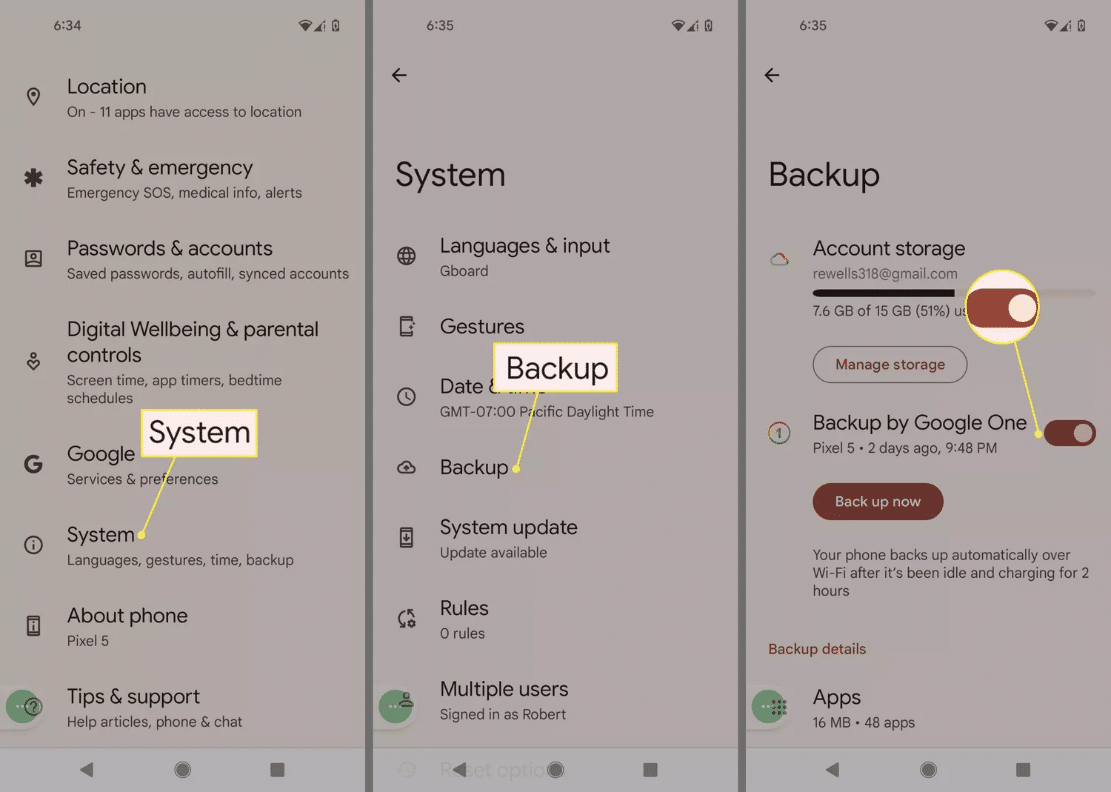
1. Back Up Your Data
To use Google’s cloud services, go to your phone’s settings. Select ‘Google’ or ‘System,’ then ‘Backup.’ If you haven’t backed up your phone before, you’ll need to turn on ‘Backup by Google One’. Finally, click on ‘Back up now’.
Whether you want to transfer your data to a new phone or not, it’s important to regularly back up your phone 2. Restore the Data
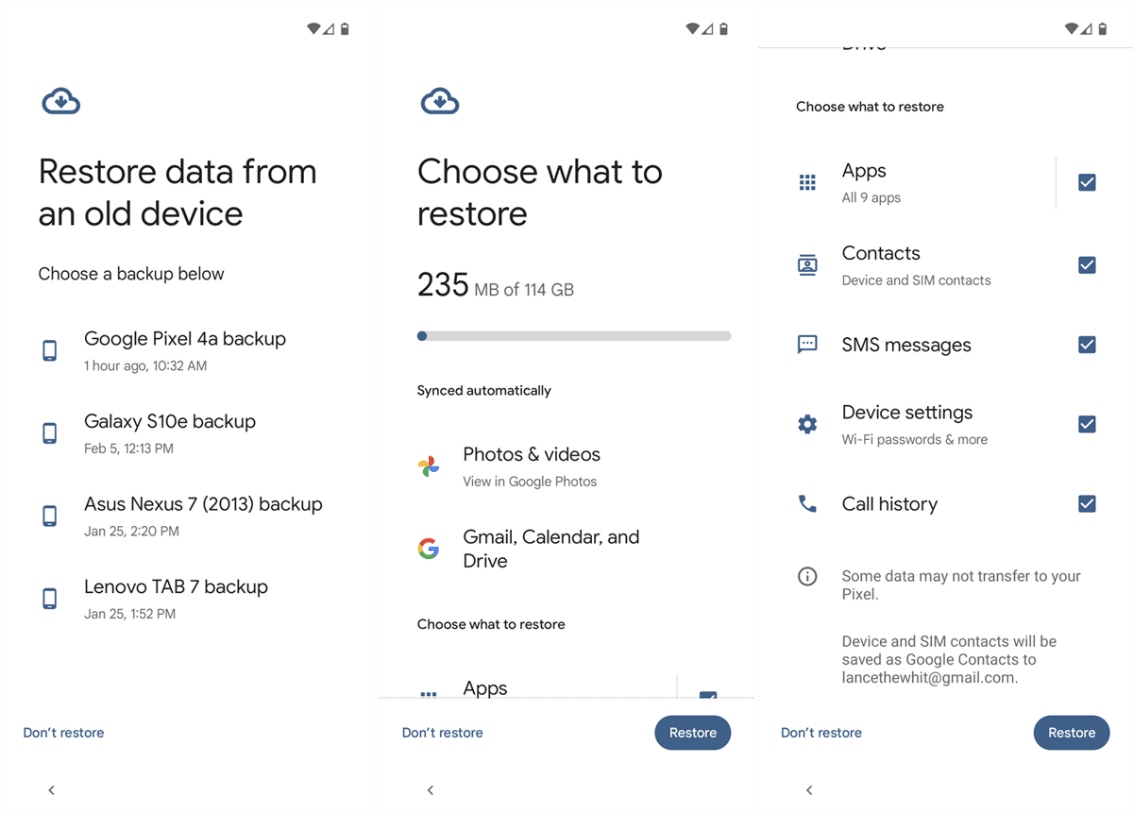
You can only restore a backup from a lower Android version to a higher Android version. The good news is that you can switch your data from one phone to another, even if you don’t have your original device anymore.
- Charge both phones (if you have your old device) and make sure you have a good Wi-Fi connection.
- Turn on your new phone and follow the instructions until you’re asked if you want to copy apps and data. Choose ‘Don’t copy’.
- When you’re given the option to use your old device, tap ‘Can’t use old device’ and then ‘OK’.
- Sign into your Google account (the one you used on your old device) and carry on setting up the phone.
- Choose your old device from the list of backup options and click ‘Restore’. For security, you’ll then be asked for the password for your old device.
You can restore backed-up data to a new phone even if you don’t have access to your old one Remote Cloning Apps
As the name suggests, remote cloning apps let you clone an Android phone remotely. They’re often used by parents who are worried about what their children are exposed to in the digital world.
One such monitoring app is uMobix. It’s designed to ensure your children’s online safety. It has location monitoring, so you can see where they are. You can even block calls and texts they receive if you feel they could be harmful.
Follow these steps to set up the app properly.-
- Get consent from the owner of the device you want to clone. This includes your children if they’re 18 or older.
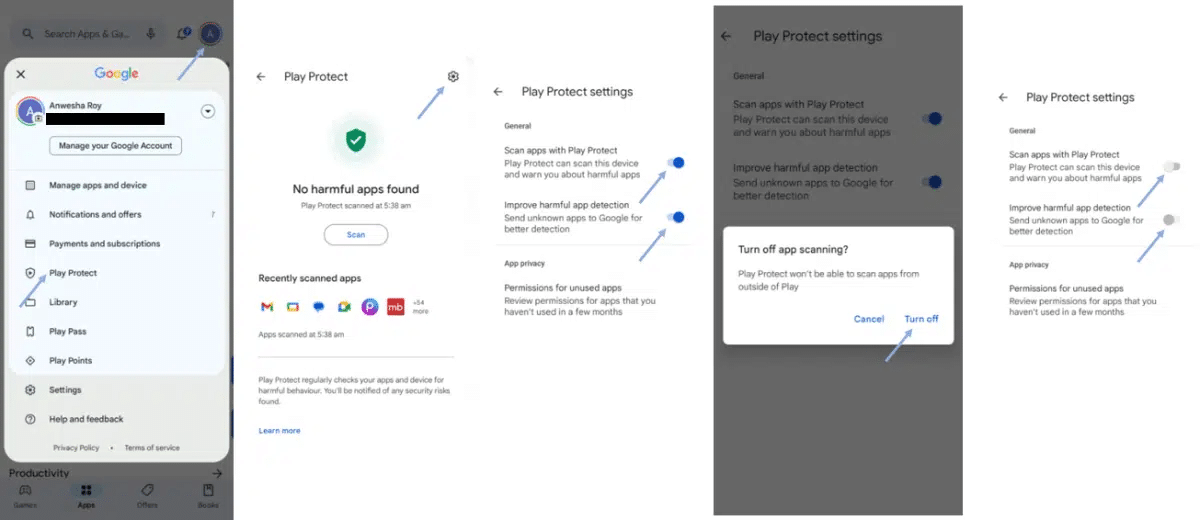
- Disable Google’s Play and Protect feature if you’re using a remote cloning app that isn’t on the Google Play Store, otherwise it’ll block the installation.
- Create an account from your chosen app’s website. The provider will email you a download link. Open the link on the phone you want to clone and follow the installation steps.
- Go to the settings and look through all the apps to find the remote monitoring app.
- Select the app and turn on all the permissions, including background data and unrestricted data use.
- Log into the app on your phone, and you should now be able to access the cloned phone’s data.
Using third-party remote cloning apps may seem like a good option, but it’s important to remember they’re not always reliable. To avoid any potential data leaks, we suggest using apps from the Play Store or legal apps that focus on protecting your data.
Network-Based Cloning
Network-based cloning is when someone – usually a hacker – exploits network vulnerabilities to launch cyberattacks or get unauthorized access to mobile devices.
Hackers scan networks for vulnerabilities they can exploit Hackers exploit network vulnerabilities to sneak past security measures, access restricted systems, and steal confidential information. One way to do so is to clone your Android phone.
Black-hat hackers do this to cause harm and for personal gain.
White-hat hackers are above board. Companies pay them to find vulnerabilities so they can be fixed before they’re exploited.
Grey-hat hackers operate in an ethically questionable area. They find vulnerabilities in a system without consent but don’t exploit them. Instead, they share this information with the hacked target, but not always for free.
So, how do hackers identify and exploit a network vulnerability?
First, hackers need to find a vulnerability, which they do using specialized scanning equipment. They then exploit these vulnerabilities using methods such as installing malware and brute-forcing passwords.
Once a vulnerability has been discovered, hackers have a window of opportunity during which they can exploit it IMEI Cloning
The IMEI (International Mobile Equipment Identity) number is a unique 15-digit serial number. Acting as your phone’s fingerprint, it contains details about the device, such as the type, make, model, and release year.
You can find the IMEI number in the ‘About phone’ section in the settings or by dialing *#06#.You can’t clone an IMEI number. Even if you could, you still couldn’t access the data on someone else’s phone with it alone, as it’s only linked to their device and not the information on it.
However, if a criminal has other personal information, such as your email address and phone number, they can use that with the IMEI to fool your network provider into carrying out a SIM swap and giving them your phone number. With this, they can access your phone, reset passwords, and steal personal information.
You can clone a phone’s SIM card, creating its exact replica. We should note that the process is illegal and carries severe consequences. It’s a technique often used by criminals to steal your phone’s identity and commit crimes.
A SIM card contains two numbers that your network provider uses to identify your phone number and you: the Ki (authentication key) and IMSI (International Mobile Subscriber Identity). From making calls to browsing the internet, SIM cards are the powerhouse behind all your network-based operations.
Someone trying to clone your SIM may use an electronic scanner to copy its IMSI and Ki. However, it’s more likely someone will try to steal your SIM card, as scanners are very difficult to get and expensive.
How to Copy a SIM Card
To duplicate a SIM card, you’ll need a blank, writable SIM card and a SIM card reader/writer.
- Put the SIM you want to clone into the card reader (first noting the IMSI number) and connect it to your computer.
- Once it’s connected, launch the reader software to copy the card’s contents using the Ki.
- Save the copied information onto your computer.
- Disconnect the reader, place the SIM into your phone, and unlock it. You’ll be asked for the PUK code (personal unblocking code), which you get by calling your network provider.
- Place the blank SIM into the card reader and connect it to the computer.
- Use the reader software to write the original SIM card’s information to the blank SIM. Enter the PUK code when prompted.
- You now have a cloned SIM card.
Once someone has cloned your SIM card and put it into their phone, they can intercept your calls and messages and access personal data (if you’ve saved this information to your SIM card).
How to Clone an Android Phone Legally and Successfully
Phone cloning is a valuable tool if you want to transfer data or monitor other phones if you do it ethically and responsibly. Here’s a handy guide to successfully and legally cloning an Android phone.
Check Operating System Requirements
Remote cloning apps may not be compatible with older operating systems, so ensure both phones meet the minimum requirements.
Also, remember that you can’t transfer your phone’s data from a higher Android version to a lower one.
Choose a Suitable Method
There are several ways you can clone a phone. Explore the different methods and choose one that is trustworthy and suits your needs. Expert opinions and user reviews are valuable sources of information.
Check Privacy Regulations
There are many legitimate reasons you may want to clone a phone, but it’s essential you respect people’s privacy. Always ask permission from the owner of the phone you want to clone.
Additionally, you should be aware of your region’s laws and regulations and the legal implications of phone cloning.
Back Up Your Data
Before you start the cloning process, back up your phone’s data. If you’re cloning someone else’s phone, back up the data on that phone, too.
Phone cloning is not 100% foolproof. This step ensures you don’t lose any information during the cloning process.
Stable Wi-Fi
Cloning a phone can take some time, so ensure both phones are connected to a stable and secure internet connection. Losing connection may mean data is corrupted or the cloning process is cut short.
Carefully Follow the Instructions
Read through all the instructions before you start the cloning process. Ensure you follow each step carefully. You may lose data if you miss a step.
Check the Process Has Been Successful
Once the cloning process has finished, check the data on both phones. All the settings, applications, and files should be there. Use the backup to replace any missing or corrupted data.
If you have any problems during the cloning process, the app’s website may contain resources to resolve these issues.
Limitations to Setting Up a Device from an Old Phone
Early mobile phones were little more than glorified radios, so it was relatively simple to intercept the signal and get the necessary codes.
Now, phones are digital, with advanced cybersecurity features that make it more difficult for someone to clone your phone without authorization and physical access.
These days, it’s almost impossible for someone to clone your phone by scanning it. Instead, they need physical access, even if only for a short time, to get the identifying numbers or install a cloning app.
One basic problem is technical limitations preventing some data and settings from being cloned. For example, some apps may not be compatible with your new phone, especially if the data is encrypted or protected by other security measures.
Additionally, the advanced security measures on newer phones, such as biometrics and encryption, make it much more difficult to clone a phone without physical access. Also, the more complex IMEI numbers are much harder to crack.
Other common issues you may encounter when cloning a phone are incompatible Android versions, software glitches, and an unreliable Wi-Fi connection.
It’s also worth mentioning that it is possible to clone Android to iOS and vice versa, but it’s a more time-consuming process.
How to Protect an Android Phone from Cloning
We increasingly rely on our mobile devices for all our activities, so it’s no wonder the risks from scams and online threats are growing. But how do you protect your online data, activities, and identity?
There are now more mobile phone contracts (8.59 billion) than people in the world.How to Stop Your Phone Being Cloned
However, all is not lost. The good news is there are some things you can do to protect yourself online.
1. Use a Strong Password
Setting a strong password, PIN, or pattern lock is your phone’s first line of defense. Use a unique one for each account.
The problem is trying to remember all those unique and complex passwords. Password managers securely store your passwords so you don’t have to remember them.
2. Regularly Update Your Phone’s Software
Ensure you’ve always got the most recent software. These updates add cool new features but, more importantly, security improvements, such as patches and bug fixes.
The updates are regularly released to fix vulnerabilities as they’re discovered to keep your device safe.
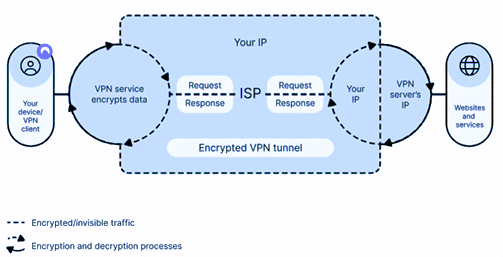
3. Use a VPN
A VPN increases your privacy and security by encrypting your online activity and sending it through a secure server. Using one makes it far more difficult for someone to intercept or monitor your data. It’s especially important if you use public Wi-Fi networks, which are generally unsecured.
A VPN allows you to browse the internet almost anonymously, protecting your data NordVPN is one of the top VPN providers due to its military-grade encryption that keeps your browsing data safe.
4. Use Reputable Apps
When downloading third-party apps, be wary of apps that ask for too many permissions, such as asking for access to your text messages, even if you download them from Google Play. Unfortunately, some trojan and malware apps find their way onto the Play Store disguised as regular apps.
Always check an app’s ratings and user reviews before hitting that download button. To verify if the app is legitimate, look for the package name and developer information, which you can find in the app settings. Then compare this information with the official app listings on the Play Store.
5. Use Two-Factor Authentication
Two-factor authentication (2FA) is a type of security that requires two separate verification methods. The three main types are something you know (your password), something you have (a code sent via SMS or email), and something you are (fingerprint or face recognition).
6. Keep Your IMEI Number Private
Keep your IMEI number private, just as you would your password. Someone with your IMEI could convince your network provider to give them your mobile number.
You may also need your IMEI number to file a police report if your phone has been cloned.
How to Tell if Your Phone’s Been Cloned
However, while these precautions make it more difficult for someone to clone your phone, it’s still possible. But how do you know if it has?
Here are a few signs that your phone or SIM has been cloned to minimize any damage :
- Your phone seems to be elsewhere: You can use this website – https://www.google.com/android/find – to check where your Android phone is. You can also use ‘Find My Device’. If your phone’s been cloned, it’ll seem to be somewhere very different from where it is, which is probably right next to you!
- You get a text asking you to restart your device: If someone has cloned your SIM, they can steal your phone number while your phone is off.
- You can’t use your phone: If your SIM card’s been cloned, you may not be able to receive or make calls or texts. That’s because someone else controls your phone number.
- There are calls and texts on your bill you don’t recognize: Someone who’s cloned your SIM card can use your phone number to make calls, all on your account. Your phone bill will probably also be much higher.
- Your phone gets slower, and the battery runs down quickly: This may happen if someone has installed spyware or malware on your phone.
Android Phone Cloning Takeaways
When used ethically and responsibly, phone cloning is a very convenient way to back up important information, transfer data from one phone to another, and keep loved ones safe.
There are many types of secure, professional phone cloning software you can use to move your digital life from one device to another safely and efficiently. Just be sure you understand the legalities of phone cloning and respect data privacy regulations.
However, some people have ulterior motives for wanting to clone your phone, so it’s important you take steps to protect yourself online.
FAQs
How do I clone my Android phone to another Android phone?
Third-party remote monitoring apps allow you to monitor all digital activity on a cloned phone from your device. Choose a reputable app with a strong security reputation. Create an account on its website, after which you’ll be emailed a download link. Download the link on the phone you want to clone and follow the instructions. Make sure you have the owner of the phone’s permission first.
How do I transfer everything from one Android phone to another?
One of the easiest ways to transfer all your data from your Android phone to another is to create a backup using Google’s cloud and restore it to your new phone. Make sure you have a secure Wi-Fi connection and that both phones are fully charged before you begin. Also, remember you can only restore a backup from a lower Android version to a higher Android version.
Can your phone be cloned without you knowing?
Yes. While it’s possible for someone to clone your phone without physical access, it isn’t easy. However, someone would only need access to your phone for a short time to clone it. That’s why it’s important you take steps to secure your digital information. If you start receiving unexpected texts or are locked out of your phone suddenly, it could be a sign that your phone has been cloned.
References
- Google Support – Back Up Your Device (Google)
- There are more mobile phones than people in the world (World Economic Forum)
Alpa Somaiya
Alpa Somaiya
View all posts by Alpa SomaiyaAlpa is a tech writer and editor with a wealth of experience in alternative finance, fintech, cryptocurrency, app security software, and the medical industry. She’s passionate about breaking down complex topics and sharing informative content that provides value.
More Spy Apps GuidesView all
Latest News View all
Biden’s Manipulated Video Will Continue To Stay On Facebook; Oversight Board Confirms
A manipulated video of Joe Biden that was recently circulated on Facebook will not be taken down because it doesn’t violate Meta’s content policy, no matter how incoherent those policies...
Bitcoin Consolidates Around $43,000 as ETF Buzz Quiets Down – Will It Reach $100,000 After Halving?
The flagship cryptocurrency, Bitcoin, has been grappling with bearish pressure following the ETF-engineered rally in early January. However, despite the depressing short-term outlook, many believe BTC could hit $100,000 after...
REGULATION & HIGH RISK INVESTMENT WARNING: Trading Forex, CFDs and Cryptocurrencies is highly speculative, carries a level of risk and may not be suitable for all investors. You may lose some or all of your invested capital, therefore you should not speculate with capital that you cannot afford to lose. The content on this site should not be considered investment advice. Investing is speculative. When investing your capital is at risk. Please note that we do receive advertising fees for directing users to open an account with the brokers/advertisers and/or for driving traffic to the advertiser website.
Crypto promotions on this site do not comply with the UK Financial Promotions Regime and is not intended for UK consumers.
© Copyright 2024 Techreport. All Rights Reserved.